XSS的魔力
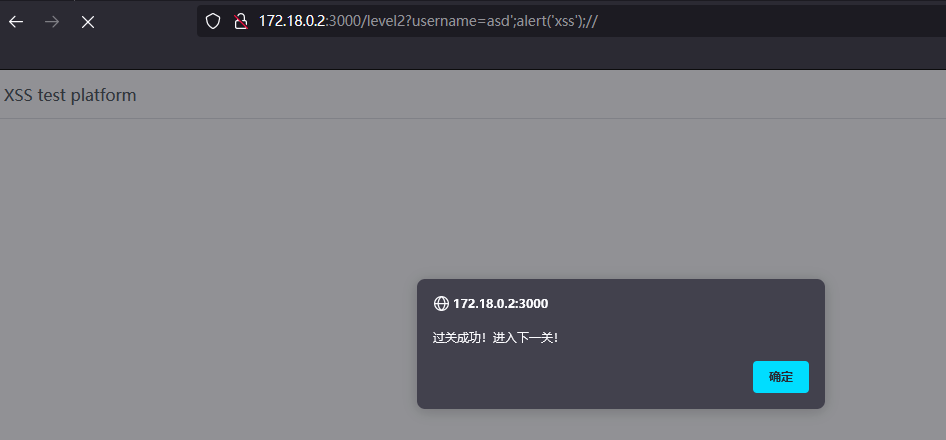
Level 2
尝试输入 “asd”,查看源码可以看到
1 | <html lang="zh"><head> |
输出点在script中
只要构造好闭合语句即可
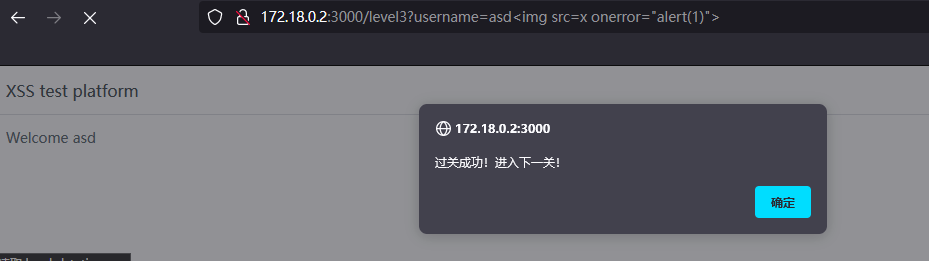
Level 3
第三关和第二关的不同在于 username 没有使用escape()函数进行转义。而在测试输入 asd’ 时候发现script处被转义
1 | <body> |
那么构造的点应该在html的div块处
Level 4
js跳转带来的xss 跳转到伪协议
1 | http://172.18.0.2:3000/level4?jumpUrl=javascript:alert() |
Level 5
1 | <html lang="zh"><head> |
表单自动提交 且action可控 控制表单提交到伪协议的地址
1 | /level5?action=javascript:alert()&autosubmit=1 |
